TimThumb was a simple, flexible, PHP script that resized images and optionally applied various filters and effects. Just about everybody that developed for WordPress used it at one time or another because of its reliability, simplicity, and ease at which it fetched remote images. TimThumb bypassed WP's expensive image functions and (arguably) got the job done more efficiently. The problem was, however, is that it evolved into a security nightmare for the developer that inherited the project, and the tens of thousands of WordPress users that relied on its use.
This article isn't current news. Originally published in 2014 on Internoetics, it simply outlines why we personally decided to stop using our (modified and secure) version of TimThumb. The article is a precursor to an image manipulation plugin upon which a number of our plugins and shortcodes will be dependent. It'll be posted in the next few days. We've reprinted this article for reference.
Since WordPress powers just about every second website, and since timthumb.php found its place as the go-to image library, the script underwent the constant scrutiny of malicious hackers because of its potential to cause significant worldwide meltdowns.
The first of TimThumb's headlining hacks came in August 2011 by way of a vulnerability  that allowed third party hackers to upload and execute arbitrary PHP code in the TimThumb cache directory, allowing the attacker to further compromise the site in any way. Despite the issue existing outside of their core responsibility, WordPress responded
that allowed third party hackers to upload and execute arbitrary PHP code in the TimThumb cache directory, allowing the attacker to further compromise the site in any way. Despite the issue existing outside of their core responsibility, WordPress responded  to the rogue code in a manner we have come to expect... but their reach was limited to their own hosted themes and plugins. TimThumb was used everywhere and its use wasn't limited to just the WordPress community; Joomla, Drupal, and standalone applications all used it. Unchecked, it means that there's likely thousands of vulnerable and insecure installations of TimThumb still being used.
to the rogue code in a manner we have come to expect... but their reach was limited to their own hosted themes and plugins. TimThumb was used everywhere and its use wasn't limited to just the WordPress community; Joomla, Drupal, and standalone applications all used it. Unchecked, it means that there's likely thousands of vulnerable and insecure installations of TimThumb still being used.
It was 2014's WebShot Code Execution Exploit  that likely proved to be TimThumb's fatal blow. The
that likely proved to be TimThumb's fatal blow. The WEBSHOT_ENABLED option that caused the security concern was disabled by default so most users of the script weren't affected, but it did diminished almost all confidence in continued use.
While timthumb.php probably ended up relatively secure, the project suffered irreparable damage and, in September of 2014, developer Ben Gillbanks sensibly decided to hang up his keyboard stating  that he felt "... responsible for a lot of the problems with TimThumb". Gillbanks claimed in a post
that he felt "... responsible for a lot of the problems with TimThumb". Gillbanks claimed in a post  to his website (at a time when a serious security issue was identified) that he hadn't used or maintained his script since before the 2011 exploit. His suggestion at the time: "Don't use TimThumb". In November of 2014 Gillbanks wrote that he had no desire to be involved with any forked versions of his product. He was clearly a happy man in doing away with the burden of such a popular (free) tool.
to his website (at a time when a serious security issue was identified) that he hadn't used or maintained his script since before the 2011 exploit. His suggestion at the time: "Don't use TimThumb". In November of 2014 Gillbanks wrote that he had no desire to be involved with any forked versions of his product. He was clearly a happy man in doing away with the burden of such a popular (free) tool.
Over the years - and after more compromising code was identified - ISPs started to scan for TimThumb so it could be removed, and WordPress prohibited it from its plugin and theme repository. Generally speaking, it's now a toxic script that just about every developer is terrified to touch. If you use it, delete or replace it. TimThumb is no longer supported or maintained.
We stripped our own version of TimThumb with every bit of code that was irrelevant and we made significant security modifications, but it was a library we hacked together and wasn't maintained as it should have been. It's only recently that we decided to replace every installation of "bmTimThumb" with another library that securely emulates the timthumb.php features... and it's this library that'll be the focus of a plugin we share in the next few days.
The general consensus is that developers should use built-in WordPress functions such as add_image_size 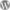 to resize images, avoiding TimThumb entirely. However, this broad recommendation might apply if we were talking about using TimThumb for just scaling thumbnails - its intended early use, and something WordPress does quite well - but the library evolved in a way that made handling local and remote images decidedly simple. It wasn't the idea of TimThumb that sucked; it was TimThumb that sucked.
to resize images, avoiding TimThumb entirely. However, this broad recommendation might apply if we were talking about using TimThumb for just scaling thumbnails - its intended early use, and something WordPress does quite well - but the library evolved in a way that made handling local and remote images decidedly simple. It wasn't the idea of TimThumb that sucked; it was TimThumb that sucked.
While TimThumb is very much a cautionary tale, the danger might lie with the developer community almost indiscriminately adding code to their projects without first fully scrutinizing the source code. The proverb "Fool me once, shame on you; fool me twice, shame on me" comes to mind (as much as I hate hearing it). Whatever solution the PHP community gravitates to in the future will likely be as secure - if not more so - than WordPress itself.
Our clients require certain features and functionality that only a library such as TimThumb can provide, and we've sourced an appropriate solution that we'll be sharing soon.
RIP, TimThumb.